
Michaël Neuman & Fabrice Weissman

Director of studies at Crash / Médecins sans Frontières, Michaël Neuman graduated in Contemporary History and International Relations (University Paris-I). He joined Médecins sans Frontières in 1999 and has worked both on the ground (Balkans, Sudan, Caucasus, West Africa) and in headquarters (New York, Paris as deputy director responsible for programmes). He has also carried out research on issues of immigration and geopolitics. He is co-editor of "Humanitarian negotiations Revealed, the MSF experience" (London: Hurst and Co, 2011). He is also the co-editor of "Saving lives and staying alive. Humanitarian Security in the Age of Risk Management" (London: Hurst and Co, 2016).

A political scientist by training, Fabrice Weissman joined Médecins sans Frontières in 1995. First as a logistician, then as project coordinator and head of mission, he has worked in many countries in conflict (Sudan, Ethiopia, Eritrea, Kosovo, Sri Lanka, etc.) and more recently in Malawi in response to natural disasters. He is the author of several articles and collective works on humanitarian action, including "In the Shadow of Just Wars. Violence, Politics and Humanitarian Action" (ed., London, Hurst & Co., 2004), "Humanitarian Negotiations Revealed. The MSF Experience" (ed., Oxford University Press, 2011) and "Saving Lives and Staying Alive. Humanitarian Security in the Age of Risk Management" (ed., London, Hurst & Co, 2016). He is also one of the main hosts of the podcast La zone critique.
2. Theories
Violence Against Aid Workers : The Meaning of Measuring
Fabrice WeissmanTranslated from French by Nina Friedman.
Quoting statistics on humanitarian insecurity in 2009, the delegate in charge of security at the International Committee of the Red Cross lamented, “the world is a riskier place to be an aid worker.”Patrick Brugger, “ICRC operational security: staff safety in armed conflict and internal violence”, International Review ofthe Red Cross, no. 874 (2009), p. 431.
Not a new observation, there is now quantitative data to support it. For the past fifteen years, researchers and consultants have been busy carrying out studies aimed at “quantifying on an objective basis”Robin Coupland, “The Role of Health-Related Data in Promoting the Security of Health Care in Armed Conflict and Other Emergencies”, International Review ofthe Red Cross, no. 889 (2013), p. 61.
violence against humanitarian workers. Relying on a variety of indicators, these analyses conclude on the whole that deliberate attacks against aid workers are increasing dramatically. They recommend improving data collection to gain a better understanding of the phenomenon for scientific, practical and political purposes. The emphasis on statistics gives rise to at least two questions: does the existing data truly indicate an increase in insecurity? How useful is this data?
The Methodological Weakness of Existing Data
Where do the Statistics on Humanitarian Insecurity Come From?
The first study on “deaths among humanitarian workers” appeared in the British Medical Journal in July 2000.Mani Sheik et al., “Deaths among Humanitarian Workers”, British MedicalJournal, 321 (2000), pp. 166-68.
Conducted by epidemiologists from the Johns Hopkins Bloomberg School of Public Health (Baltimore) with WHO support, it looked at the deaths reported by thirty-two “humanitarian organisations” during the period 1985 to 1998. Johns Hopkins researchers also participated in two cross-sectional studies assessing the prevalence of non-lethal violenceCate Buchanan and Robert Muggah, “No Relief: Surveying the effects of gun violence on humanitarian and development personnel”, Geneva: Centre for Humanitarian Dialogue, Small Arms Survey, June 2005.
and the risk of violence-related morbidity/mortality in the aid sector.Elizabeth A. Rowley et al., “Violence-Related Mortality and Morbidity of Humanitarian Workers”, American JournalofDisasterMedicine, vol. 3, no. 1, 2008, pp. 39-45.
Accessible online, the Aid Worker Security Database (AWSD)See https://aidworkersecurity.org/, last accessed 29 December 2015.
is meant to record every “major incident of violence against aid workers” (i.e. “killings, kidnappings and attacks that result in serious injury”) reported by the media and aid operators since 1997. An offshoot of a 2006 study conducted for the Overseas Development Institute (ODI) and the Center on International Cooperation,Abby Stoddard et al., “Providing Aid in Insecure Environments: Trends in Policy and Operations”, HPG Report 23, London: Overseas Development Institute, 2006.
the AWSD is now kept up-to-date by Humanitarian Outcomes (HO), a consulting firm set up by the authors of the 2006 study. HO releases an annual report on the security of aid workers, the source of data most frequently cited by the media, the United Nations, NGOs and humanitarian security experts.See https://aidworkersecurity.org/citations, last accessed 29 December 2015.
AWSD figures and analyses will be the main subject of this chapter.
With the Insecurity Insight group,See www.insecurityinsight.org, last accessed 29 December 2015.
a third source of statistics appeared in 2008. The group, comprising two academics (a statistician and a conflict specialist), a medical advisor from the International Committee of the Red Cross (ICRC) and a humanitarian consultant, has developed in partnership with several NGOs its own database, the Security in Numbers Database (SiND).Christina Wille, “The six ‘Ws’ of security policy-making”, Humanitarian Exchange Magazine, no. 47, 2010, pp. 6-8.
Insecurity Insight also contributes to quantitative studies conducted by the ICRC as part of its Health Care in Danger campaign launched in 2011.ICRC, “Health care in danger: a sixteen-country study”, Geneva: ICRC, 2011; ICRC, “Violent Incidents Affecting Health Care. January to December 2012”, Geneva: ICRC, 2013.
How Accurate are the Indicators?
All of these studies claim to be “evidence-based”, but careful reading reveals several methodological weaknesses. The first stems from the indicators selected to translate the abstract concepts of insecurity, danger and violence into quantitative data. While the AWSD and Johns Hopkins look at the number of aid workers killed, injured or kidnapped, the ICRC and Insecurity Insight studies count all security events affecting humanitarian work or healthcare—considered a more pertinent indicator for describing the daily violence hampering humanitarian action. Thus, in addition to attacks against personnel, they record incidents as varied as bombings, thefts of supplies and equipment, arrests of patients, threats or damage to the aid agencies’ reputation, water shortages and electricity outages, and administrative obstacles.
With no precise boundaries, the notion of an “incident affecting humanitarian work” is extremely vague and subject to interpretation, and this weakens its value as an accurate and meaningful indicator. The better defined category of “aid workers killed, injured or kidnapped” is not much easier to use, necessitating as it does that one should determine whether the victims were harmed as a result of their work, and whether that work was “humanitarian”. There is of course no generally accepted definition of “humanitarian work” among practitioners, researchers, authorities, military personnel or journalists. The first Johns Hopkins mortality study counted UN peacekeeping forces among humanitarian organisations, whereas the AWSD excludes armed forces, human rights workers and people working on “reconstruction projects.” Instead, it defines aid workers as national and international employees and commercial subcontractors of “not-for-profit aid agencies [...] that provide material and technical assistance in humanitarian relief contexts.” This somewhat tautological definition leaves those tasked with updating the database much room for interpretation. In reality, the “aid worker” category is applied to a wide range of actors who differ in terms of status, functions, practices and, therefore, exposure to danger: representatives of foreign governments and funding bodies; UN officials and employees; representatives of the ICRC and the Federation; national Red Cross and Red Crescent society volunteers; employees of international and local NGOs; members of religious and community solidarity networks; employees of transport and private security companies, etc.
Determining whether attacks are related to the victims’ work is also problematic, particularly for national staff(over 90 per cent of workers) who, in addition to their professional activities, are exposed to “ordinary” crime and war-related violence. In practice, the databases and studies record every event affecting an aid sector employee or subcontractor, whatever the circumstances. In Syria, for example, the AWSD records national employees killed when their homes were bombed, in an attack on a market, or when the relief convoy they were escorting was machine-gunned. Similarly, in Afghanistan, it counts international staff killed in an attack on a restaurant, while hiking in the forest, during a domestic burglary or during an attack on the hospital where they were working.
How Reliable are the Techniques Used to Collect the Data?
The imprecision of the indicators is further increased by the bias of the methods used to collect the data. The AWSD and SiND databases, as well as the Johns Hopkins epidemiological studies, count attacks and victims based on their reporting in the administrative records of aid organisations and/or the media. AWSD investigators, for instance, rely on information from “public sources, through systematic media filtering [in particular, ReliefWeb and US State Department reports], and provided directly to the project by aid organisations”See https://aidworkersecurity.org/about, last accessed 29 December 2015. such as UNDSS, regional security consortiums and MSF.
There is a flaw in this method that is well-known to security specialists: it does not determine whether it is the phenomenon being studied (the violence) that is changing, its reporting (documenting by administrative departments in humanitarian organisations or the media) or some combination of the two.These obstacles are comparable to those encountered when quantifying crime in France, for example. See Renée Zauberman et al., “L’acteur et la mesure: Le comptage de la délinquance entre données administratives et enquêtes”, Revue française de sociologie, vol. 50, no. 1, 2009, p. 31. However reliable, media coverage of attacks against aid workers depends on several factors: the number of journalists in the country concerned and the extent of their interest in humanitarian security issues; the nationality of the victims; the transparency of the aid organisations; the feasibility of investigation, etc. Similarly, the systems used by humanitarian organisations to collect security data have improved considerably over the past twenty years, gradually leading to an increase in the type and number of attacks reported. Even so, reporting and transmission of information is still highly dependent on the proactivity of managers, how much resistance they encounter in their organisation, and how much importance their personnel attach to security issues. This can vary greatly over both time and space; while some volunteers are reluctant to collect data on violent incidents,Koenraad Van Brabant, an advocate of professionalised humanitarian security, observes that there is much resistance when introducing security data collection, due to the fact that it might bring professional errors to light, tarnish the image of certain operations and jeopardise their existence, as well as the funding and employment contracts that depend on them. Koenraad Van Brabant, “Incident Statistics in Aid Worker Safety and Security Management: Using and Producing Them”, London: European Interagency Security Forum, 2012.
others are inclined to report any type of event likely to affect their security.As the French national observatory for violence in healthcare settings (Observatoire national des violences en milieu de santé, or ONVS, created in 2005) writes [translation]: “the number ofreports does not reflect how dangerous a healthcare site is, but rather the number of times professionals felt it important to report. This varies widely from one facility to another, from one department to another and, at a given healthcare site, from one year to another (...). Raw data have little meaning in themselves, but illustrate situations experienced in the facilities, the awareness of the actors and the promotion of preventive actions”. See “Observatoire national des violences en milieu de santé. Rapport annuel 2012”, Paris: Ministry ofSocial Affairs and Health, January 2013, p. 3.
Therefore, it is difficult to distinguish between changes in violence and changes in the way it is reported, both administratively and in the media. This uncertainty is particularly pronounced for events whose definition is open to interpretation (such as attacks resulting in “serious injuries”)See Chapter 6, box, “The Case of ‘Dangerous Patients’ in Yemen’s Governorate of Amran”, p. 103. Similarly the French national observatory for violence in healthcare settings notices that two different facilities report as “serious assault on the physical integrity of health personnel” the following events [translation]: “while saying hello, the patient shook violently my left wrist. I asked him to stop, he did not. I screamed and the staff arrived”; and “when putting the patient in an isolation room, he pulled out a knife. We just had time to close the door. He refused to drop the knife and threatened with death the health assistant and other staff members.” Ibid.
and incidents involving national staff (the reporting of which is even more erratic).
Studies attempting to calculate attack and victim rates (number of violent events and victims, respectively, per 100,000 workers per year) face a further obstacle: the lack of a reliable denominator. Rare is the organisation able to provide accurate figures on its workforce by country and by year, and so, for example, the AWSD is forced to put forward a rough estimate of the number of humanitarian workers based on standard budget to national and international staff" ratios. See www.humanitarianoutcomes.org/gdho/methodology, last accessed 29 December 2015.
Moreover, aside from the AWSD database, all of the studies use samples for which there is no explicit sampling method, other than the ability of the organisations consulted to supply data for the study. Yet they generalise their results to the entire aid sector.
Most of the authors acknowledge that their datasets are neither “complete” nor “fully representative,”Christina Wille and Larissa Fast, “Operating in Insecurity: Shifting patterns of violence against humanitarian aid providers and their staff (1996-2010)”, Switzerland: Insecurity Insight, 2013, p. 3.
that there are “incomplete or missing records”Sheik et al., op. cit., p. 167.
and that the data is “to a degree, inaccurate”,Coupland, op. cit., p. 65.
particularly with respect to national staff. But they have no doubts about the solidity of the conclusions they draw from them; the Johns Hopkins researchers, for example, “believe the findings to be representative”Sheik et al., op. cit., p. 167.
and Humanitarian Outcomes claims that the “AWSD remains the sole comprehensive global source of this data, providing the evidence base for analysis of the changing security environment.”See https://aidworkersecurity.org/, last accessed 29 December 2015.
The Debatable Interpretation of Trends
The Hidden Stability of Victim Rates
All the studies and quantitative analyses conclude, like Insecurity Insight, that there are “rising burdens of insecurity for aid workers.”Wille and Fast, op. cit., p. 3.
The Johns Hopkins group claims, “Our findings confirm the belief that deaths among humanitarian workers have increased (...) Humans with weapons rather than motor vehicles pose the greatest threat.”Sheik et al., op. cit., pp. 166-68.
Similarly, the ODI/HO studies stress the steady decline in security conditions since at least 1997. “Both the numbers of attacks on humanitarian aid operations and the victims they claimed reached their highest point since data has been systematically collected,”Abby Stoddard et al., “Unsafe Passage: Road attacks and their impact on humanitarian operations”, Aid Worker Security Report 2014, London: Humanitarian Outcomes, August 2014, p. 2.
declared Humanitarian Outcomes in its 2014 annual report.
The details in these studies, however, hint at a more nuanced situation. Published in 2000, the first Johns Hopkins mortality study described a bell curve: a sharp increase in deaths (all causes combined) from 1985 to 1994—the year of the genocide in Rwanda—followed by a decline from 1995 to 1998. It added that these changes went hand-in-hand with the increase in humanitarian agencies and workers in the field. But, with no data on the number of people deployed, it was unable to draw any conclusions about the change in risk.
This was precisely the limitation that the ODI/HO studies sought to overcome. Estimating the transformation in the humanitarian workforce, they calculated the variation in the attack rates (number of security events per 100,000 workers per year) and victim rates (number of people killed, injured or kidnapped per 100,000 workers per year). Unlike the absolute data, the relative data received little public attention. The AWSD website only provides graphs illustrating the trebling of the attack rate from 1997 to 2012See https://aidworkersecurity.org/incidents/report/rates, last accessed 29 December 2015.
(cf. figure 1) while victim rates are only mentioned in three reports—in 2006,Stoddard et al., “Providing Aid in Insecure Environments”, op. cit.
2009Abby Stoddard et al., “Providing Aid in Insecure Environments: 2009 Update”, HPG Policy Brief No. 34, London: Overseas Development Institute, 2009.
and 2013.Adele Harmer et al., “The New Normal: Coping with the kidnapping threat”, Humanitarian Security Report 2013, London: Humanitarian Outcomes, October 2013.
Yet, whereas the annual number of victims has quadrupled in absolute terms over the past fifteen years (from seventy-eight for the 1997-2001 period to 376 in 2012-2013, cf. table 1), in relative terms it has remained remarkably stable; from 1997 to 2012, the number of workers killed, injured or kidnapped per 100,000 per year fluctuated between forty and sixty (cf. figure 2).This figure is of the same order as the risk of violent incidents causing death or injuries estimated by Johns Hopkins to be six per 10,000 per year between 2002 and 2005. Rowley et al., op. cit.
In other words, according to AWSD’s own data, the number of victims has increased in proportion to the number of aid workers. In this sense, humanitarian action is no more dangerous than it was in the past. The risk of violent death may even be dropping, if we believe the decline in the percentage of deaths among victims (from 49 per cent in 1997-2001 to 30 per cent in 2012-2013, according to the author’s calculations using the AWSD database). Surprisingly, the 2013 report draws the opposite conclusion, stating in its summary that the “number of victims relative to the estimated total number of aid workers (...) continued to rise.”HO’s consultants justify the way they present their results with the need to produce reports that are “a kind of reminder to political actors that humanitarian aid work is quite a dangerous job” (interview with a senior Humanitarian Outcomes consultant, 16 April 2015).
See https://aidworkersecurity.org/incidents/report/rates, 29 December 2015.
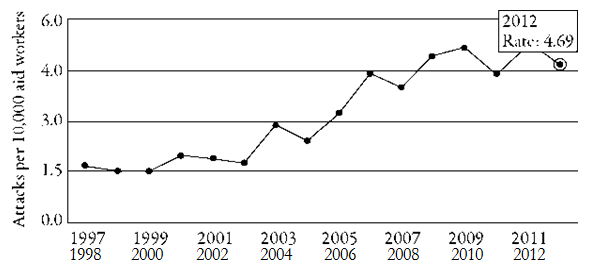
Rate of violence for all staff, 1997-2013
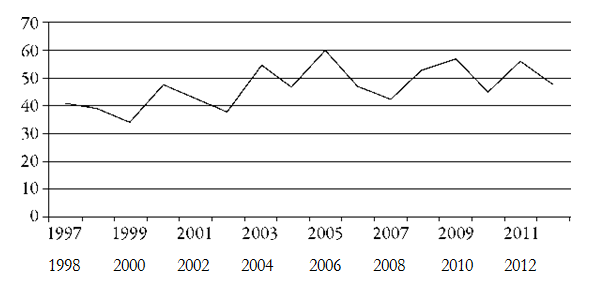
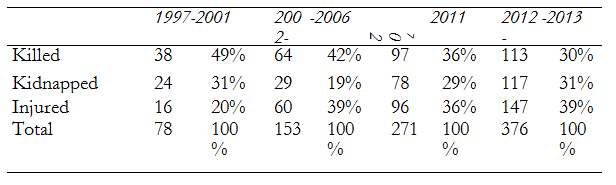
Table 1: Number of victims among humanitarian personnel, yearly average (sources: AWSD, author’s calculations)
No Global Trend
The overall stability of the rates—like the overall increase in the absolute number of victims—masks wide disparities between different countries and different years. More than half of the deaths considered by Johns Hopkins from 1985 to 1998 occurred in the African Great Lakes region and the Horn of Africa. And three-quarters of the victims listed by the AWSD since 1997 have been in only six or seven countries.In 2014, the violence was even more concentrated, with three-quarters occurring in Afghanistan, Pakistan, Syria and the two Sudans.
Even among the highest-risk countries, the homicide rate for humanitarian workers varies widely. According to the 2012 AWSD report,Abby Stoddard et al., “Host States and Their Impact on Security for Humanitarian Operations”, Aid Worker Security Report 2012, London: Humanitarian Outcomes, December 2012, p. 4.
for the period 2006-2011, it ranged from 3/100,000/year in the Democratic Republic of Congo (the same order of magnitude as the homicide rate in the United States) to 9/100,000/year in the two Sudans, Afghanistan and Pakistan, to 17/100,000/year in Central African Republic, to 37/100,000/year in Sri Lanka, and to 58/100,000/year in Somalia.
It is difficult to establish whether these rates reveal that humanitarian workers are more exposed than other people. This would require comparing them to the homicide rate within the population as a whole or to other categories such as journalists, small traders, truckers, etc. It should be emphasised, however, that homicide rates for humanitarian workers are lower than that of fatal accidents among the most dangerous civilian professions in the United States, namely logging workers (91 deaths per 100,000 workers per year), fishermen (75/100,000/year) and aircraft pilots and flight engineers (50/100,000/year).U.S. Bureau of Labor Statistics, U.S. Department of Labor, 2015, www.bls.gov/ iif/oshwc/cfoi/cfch0012.pdf, last accessed 29 December 2015.
Contradictory Interpretation of the Observed Variations
ODI/HO interprets the rarity of attacks in the majority of settings as proof of “improved security management throughout the humanitarian community.”Abby Stoddard et al., “Spotlight on security for national aid workers: Issues and perspectives”, Aid Worker Security Report 2011, Humanitarian Outcomes, August 2010, p. 3.That is, the professionalism of aid actors has helped protect relief workers, including in situations “marked by high crime or societal disruption”. They explain the abnormally high death rate in the six or seven highest-risk countries by the extremism and unbridled violence of the belligerents, which no amount of protection can counter. In other words, while improved security conditions can be credited to aid actors, worsening security can be blamed on the assailants.
Insecurity Insight, on the other hand, attributes increased insecurity to “greater humanitarian presence in dangerous contexts,” particularly in “areas of active fighting and [in] urban areas, where crime is a bigger issue.” Subject to pressure by the media and funders, they say, humanitarian actors show “higher risk tolerance”, working in environments from which they would, in the past, have withdrawn.Wille and Fast, op. cit., p. 23.
The data exploited in these studies cannot be used to determine which of these interpretations is correct, even in a given country or situation. A qualitative approach is needed to distinguish between changes that are due to the context and those due to the practices of aid agencies. In this case, neither ODI/HO nor Insecurity Insight offer empirical evidence to justify their preferred interpretations. These appear to mirror their preconceptions regarding insecurity, with Insecurity Insight lamenting an aid system resigned to losing personnel and HO bemoaning a world that has become increasingly violent toward humanitarian workers.
The Question of Targeting
Finally, the ODI/HO studies aimed “to measure to what extent aid workers were targeted specifically for reasons related to their mission.”Stoddard et al., “Providing Aid in Insecure Environments”, op. cit., p. 19.
To achieve this, they calculated the respective proportions of “incidental” violence unrelated to the fact that the victims were aid workers (“wrong time, wrong place”), and “political” and “economic” violence, targeting aid workers as such (“because they were aid workers”).
They concluded that the majority of attacks listed since 1997 were political rather than incidental. More precisely, aid workers were said to be targeted because they are “perceived to be aligned or equated with another party (the US, the West, the UN)”. As, for example, HO explained in 2011, “[Antipathy toward an international humanitarian presence perceived as Western-aligned, continue[s] to drive overall trends in attack numbers.”Stoddard et al., “Spotlight on Security for National Aid Workers”, op. cit., p. 3.
Sri Lanka and the Palestinian Occupied Territories were, however, considered exceptions to the rule. The high humanitarian worker death rate from 2006 to 2011 was felt to be incidental—“collateral damage” caused by intense fighting.
The authors of the 2006 initial study clarify that they were, however, unable to make “a reasonable judgment as to motivations”Stoddard et al., “Providing Aid in Insecure Environments”, op. cit., p. 19.
of the attackers in three out of five cases. In fact, it is often difficult to identify the perpetrators and their sponsors with any certainty, and even less to know their intentions and primary targets. Were they targeting the individual in a private capacity, the various institutions that the victim represented—employer, family, government, nation, patron, neighbourhood, political party, social class, religious or ethnic community—or an unrelated third party?
In practice, ODI/HO reports provide no quantitative (or qualitative) data demonstrating that humanitarian actors are targeted primarily because they represent an aid sector equated with the West, rather than because of a perception that they are bad bosses, malevolent doctors, economic competitors or allies of the opposition. The hypothesis attributing violence against humanitarian workers to their real or assumed lack of neutrality is, on the contrary, belied by ODI/HO’s own data, with the 2006 report showing no correlation between the number of violent events and the presence of Western troops or UN integrated missions,Ibid., p. 1.
and the 2013 report describing an increase in the number of attacks in Afghanistan—after the withdrawal of NATO troops.Stoddard et al., “Unsafe Passage”, op. cit., p. 6.
In fact, the hypothesis that the violence is associated with the “undeniably Western nature and orientation of much of the international aid community”Stoddard et al., “Providing Aid in Insecure Environments: 2009 update”, op. cit., pp. 5-6.
obscures the political transactions upon which the security of humanitarian actors depends. As we have shown elsewhere,Claire Magone et al. (eds), Humanitarian Negotiations Revealed: The MSF Experience, London: Hurst & Co, 2012.
relief operation deployment depends not on abstract principles such as neutrality, impartiality and independence, but on negotiating an acceptable compromise with the various forces present, at the intersection of the different parties’ interests and constraints. To put it bluntly, the protection of aid actors depends on their ability to find an acceptable way—if there is one—to be more useful alive than dead to those committing the violence. And there is no evidence to suggest that their “Western nature” is an insurmountable obstacle to this; indeed, the impressive ICRC and MSF deployment in Afghanistan—ten years after being among the Taliban’s primary designated targets—demonstrates quite the opposite.
The Production of Ignorance
Is Increasing Humanitarian Insecurity a “Myth”?
In summary, quantitative studies on humanitarian insecurity are based on unreliable indicators whose ambiguous meaning is systematically interpreted in such a way that confirms the preconception that danger is escalating. Does this mean that increasing humanitarian insecurity is a “myth”, as, for example, criminologist Arnaud Dandoy and political scientist Marc-Antoine Perouse de MontclosArnaud Dandoy and Marc-Antoine Pérouse de Montclos, “Humanitarian Workers in Peril? Deconstructing the myth of the new and growing threat to humanitarian workers”, Global Crime, vol. 14, no. 4, 2013, pp. 341-58.
claim?
As these two authors rightly point out, the history of humanitarian action has been punctuated by deliberate attacks against aid workers, from the 1870 Franco-Prussian War through both World Wars, the wars of independence and the Cold War to the extreme crises of the 1990s.See Chapter 3, p. 67.
As for the past fifteen years, some findings might withstand critical examination of the existing data: while there has been an increase in the absolute number of humanitarian workers killed, injured or kidnapped, this increase appears to be proportional to the growing number of humanitarian personnel.Moreover, the majority of incidents are concentrated in a small number of countries. Serious attacks against aid workers are therefore neither new, nor widespread, nor growing in relative terms.
This does not mean, however, that the rise in insecurity is a myth or that the concerns expressed by aid actors are irrational. The evolution in attacks against humanitarian workers indistinctively reflects developments in the political and military context and in the security practices of aid organisations. In this sense, the relative stability in the victim rate since 1997 may conceal a worsening security environment compensated by better protection measures and/or the withdrawal of aid organisations from the most dangerous areas.See Chapter 1, p. 1.
In any event, interpreting trends requires using other sources—qualitative, in particular—to evaluate how dangers and security practices are changing, context by context.
“Not everything that counts can be counted” (Albert Einstein)Quote attributed to Albert Einstein, taken from Christine Fassert, “‘Tout ce qui compte ne peut être compté’: la (non-) fabrication d’un indicateur de sécurité dans le contrôle aérien”, Sociologie et sociétés, vol. 43, no. 2, 2011, p. 249.
And yet aid actors and specialists are less concerned with rounding out quantitative studies with historical or sociological approaches than with producing better and more complete, accurate and reliable figures. This predilection for numbers—despite their weak descriptive or analytical power—has mainly to do with the agenda of those doing the quantifying. “What gets counted gets done!” says, for example, an author of an ICRC study, whose stated goal was to produce “reliable data” to influence “the policies of all stakeholders [...] in favour of greater security of effective and impartial health care in armed conflict.”Coupland, op. cit., p. 66.
Hence the primary goal of producing numbers is not to understand the mechanisms behind the attacks, but to denounce their existence (without having to describe them in detail). Reinforcing edifying narratives, the data are used to construct a new, intolerable moral around the violence done to humanitarian workers, and more particularly healthcare workers.
Indeed, the very notion of attacks against humanitarian workers suggests that they are targeted because of their status by attackers who reject the values of humanism and solidarity these workers claim to represent; or, that they are hurt in spite of their status, which is supposed to protect them by virtue of their “exceptional” social and moral value.On the humanitarian exceptionalism construct, see Larissa Fast, Aid in Danger: The Perils and Promise ofHumanitarianism, Philadelphia : University ofPennsylvania Press, 2014.
In either case, aid actors are seen as the heroic victims of evil incarnate or of cynical usurpers who have weakened the protective powers of their logos. The codes and formalism of science are used to bolster this view by treating weak, equivocal insecurity data as facts that “cannot reasonably be questioned.”Coupland, op. cit., p. 66.
The legitimacy and effectiveness of such an activist strategy are questionable. As Patrice Bourdelais and Didier Fassin remind us, the construction of one intolerable is inseparable from tolerance for another intolerable.Didier Fassin and Patrice Bourdelais (eds), Les constructions de l’intolérable. Etudes d’anthropologie et d’histoire sur les frontières de l’espace moral, Paris : La Découverte, 2005.
In this case, defending humanitarians in danger has replaced defending populations in danger—the focus of public opinion campaigns by aid actors in the 1990s. It is not evident that humanitarians, as a group, should be more sacrosanct than journalists, small traders, farmers, drivers, mechanics, or non-combatants in general. Also questionable is the political efficacy of campaigns that refuse to name the perpetrators of serious violence—or even the countries where it occurs in the case of the ICRC—in order “to avoid giving rise to political controversy.”ICRC, “Violent Incidents Affecting Health Care: January to December 2012”, op. cit., p. 2 n. 5.
However, the biggest problem with abusing quantitative data for activist purposes is that it produces ignorance. Beyond the uncertainty surrounding the reliability and meaning of the statistics, global figures convey the misleading notion that the violence is a global phenomenon obeying general laws.In the words of social philosopher Alasdair MacIntyre, “seeking a unified theory of violent behaviour makes no more sense than seeking a single explanation for quick behaviour.” Just as there is an infinite variety of reasons for doing things quickly, there is an infinite variety of reasons for behaving violently toward a person working (or not) for a relief organisation. See Human Security Report 2013— The Decline in Global Violence: Evidence, Explanation, and Contestation, Simon Fraser University, Vancouver: Human Security Research Group, 2014, p. 42.
In practice, searching for common causes results in the dominant prejudices in the aid world—attributing insecurity to the lack of real or assumed neutrality as well as to anti-Western sentiment—being presented as scientific fact. They also result in relatively infrequent, heterogeneous events in a wide range of volatile settings being lumped together into a single aggregate in the hopes of detecting statistically significant trends, probabilities and risk factors. Sometimes comparing violence to a disease, such global quantitative approaches nourish the illusion that security dilemmas can be clarified, or even solved, by mathematically calculating incidence rates and risk-benefit ratios.
In so doing, quantitative studies divert the attention of practitioners and specialists away from the real challenge, which is to analyse each major security event, to place it in the local historical context and that of the relief operation, to discuss the practices that contributed to its occurrence (or mitigation) and whether the risks were worth taking. In order to understand and prevent violence, we must tackle the sensitive questions hidden by the quantification exercise—in particular, who is perpetrating the violence, and which mistakes, if any, are aid actors making? This is not to say, of course, that we should abandon all efforts to quantify. For a particular organisation or situation, keeping count of violent acts that result in human and material damage is necessary, if only to facilitate their qualitative analysis. While it is important to record incidents scrupulously, it is even more urgent to use substantiated accounts in order to understand how and why they happened.
Box: Security Incident Narratives Buried in Numbers: The MSF Example
Fabrice WeissmanTranslated from French by Justin Hillier.
Since 1971, thirteen international staff members have been killed while on assignment with MSF. Five volunteers were assassinated in Somalia (1997, 2008 and 2011),On 20 June 1997, an MSF-France doctor was murdered at a hospital in Baidoa by the comrade of a hospitalised militiaman who had died the previous day. On 28 January 2008, a surgeon and a logistician working for MSF-Holland were killed along with their driver when the vehicle they were travelling in was hit by a remote-controlled bomb in Kismayo. On 29 December 2011, MSF-Belgium’s head of mission and a medical coordinator were killed in their office in Mogadishu by a recently fired employee.
four in Afghanistan (1990 and 2004),On 28 April 1990, an MSF-France logistician was killed in an advanced medical post in Yaftal in Badakhshan. On 2 June 2004, a project coordinator, doctor and logistician working for MSF-Holland died with their driver and translator when local fighters in Baghdis province opened fire on their car with automatic weapons.
two in Sudan (1989),On 21 December 1989, an Aviation Sans Frontières plane was shot down while taking off from Aweil, killing its pilot and three passengers: a doctor and a logistician working for MSF-France and a World Food Programme technician.one in Angola (1992)On 13 November 1992, an MSF-Belgium logistician died from his wounds after being attacked during an armed burglary.
and one in Central African Republic (2007).On 11 June 2007, an MSF-France logistician died from her wounds after her car was ambushed, apparently mistakenly, by rebels in the Ngaoundai region in north-west Central African Republic.
However, there has been no reliable data on the number of national employees who have been killed while on mission or on the number of staff (national or international) seriously injured or kidnapped since the founding of MSF.
In 2009, in response to this lack of information and confirming the recommendations provided by security specialists,See Chapter 5, p. 71.MSF introduced a system to collect data on safety and security incidents known as SINDY.“Safety & Security Incidents & Accidents” database, MSF-Belgium, Brussels, 15 December 2009.
Developed by MSF-Belgium, all MSF operational sections progressively adopted (and adapted) SINDY via their respective security advisors.
Directly updated by the teams in the field, the database is restricted to the organisation’s managers, who have access rights which vary according to their level of responsibility.For example, a head of mission can only look up incidents that occurred in the country where he or she works, whereas the director of operations and the security advisor have rights to the entire database.
SINDY combines three functions: centralised archiving for incident reports,Using a standard form to which any type of document can be attached. quantitative data collectionSINDY’s interface requests a user to describe each incident, guided by fields and drop-down menus with predetermined options: location; time; weapon(s) used; type of tactical situation (ambush, gunfire, bombing, etc.); types of violence (armed, sexual, etc.); victim profile; mission profile; financial, human and operational impact; crisis management procedure implemented, etc.
and an alert system.Each incident logged in the database triggers an email notification sent to all subscribers.
Each MSF operational section has its own database to which it alone has access, although this does not prevent the occasional sharing of incident or summary reports.
SINDY’s scope of application varies from one section to another. Whether safety incidents (road accidents, blood exposure, electrical accidents, etc.) are recorded or not, SINDY’s various databases are based on disparate case definitions. For instance, MSF-France restricts encoding to moderate and severe security incidents with consequences on property or peopleMSF-France classifies as “severe” any violent action against MSF staff, patient or property causing death or serious injury (incapacity to work), rape, kidnapping, theft and material damage valued at €10,000 or more. “Moderate” describes incidents that had the potential to become a severe incident (threats or near-miss incidents) and any other incident the field deemed important to log in the database (to keep a record and share easily, notify the chain of command, etc.) OCP (Operational Centre Paris) SINDY User Manual, Paris: MSF, November 2013, p. 8.
whereas MSF-Belgium asks users to log any security and safety incident presenting a high, medium or low risk to property, people or operations.SINDY 2, Security Focal Point, Brussels: MSF-OCB (Operational Centre Brussels), December 2010, p. 3.
MSF-Spain has extended the database to events affecting “the acceptance and/or neutrality of MSF.”OCA (Operational Centre Amsterdam), Comparison of Severity Classification of Security Incidents between OCs with the idea to streamline between sections, May 2015.
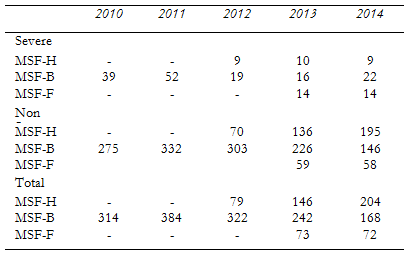
To date, SINDY has been primarily used by security adviors to produce annual year-end quantitative reports on security management; a summary for the year 2014 is provided below for the three main operational centres (Belgium, France, Holland). All the reports highlight that theft and threats make up the majority of incidents reported, while warning against making hasty interpretations of this data given the reporting bias observed in the field. MSF-Belgium underlines that the sharp fall in the number of incidents recorded in 2014 (cf. Table 2) “is not linked with a real decrease of incidents in the field but with the fact of the decrease of the reporting itself.”Overview of OCB Risk Management (SINDY 2014 Report), Brussels: MSF- OCB, November 2014, p. 2.
Conversely, the Dutch section attributes the increased number of incidents seen in 2014 to its improved reporting system but also to the fact that “respect for independent humanitarian action is diminishing.”Overview of OCA Security Incidents (SINDY 2014 Report), Amsterdam: MSF- OCA, February 2015, p. 7.
MSF-Holland and MSF-France reports are alone in including a succinct description of the circumstances and consequences of the most serious events recorded in 2014, such as the unresolved abduction of four Congolese employees in the Democratic Republic of Congo in 2013, the murder of nineteen people (including one patient and three national staff members) at two hospitals managed by MSF in Central African Republic, the detention since 2012 of a national staff member in Burma and the looting and destruction of three hospitals in South Sudan. Deprived of the benefit of a more detailed description, MSF-Belgium’s report lauds the fact that, in 2014, the organisation “did not face a strong increase in severe incidents [showing] the capacity of the organisation to adapt and work in very sensitive contexts.”Overview of OCB Risk Management (SINDY 2014 Report), Brussels: MSF- OCB, November 2014, p. 8.
The report makes no mention of the kidnap that same year in Syria of the five expatriates working for the Belgium section who were freed between three and five months later after being held in particularly harsh conditions.
The quantitative approach to insecurity adopted by MSF and the way it is used reveal the same failings generally observed in other similar databases, such as the Aid Worker Security Database.See Chapter 4, p. 55.
Relying on ambiguous definitions without any consistency between sections, MSF’s data is diminished by significant reporting biasThe bias identified by the security advisors (in the knowledge that SINDY quantifies the number of security incidents entered in the database and not the “actual” number of incidents that occur) has been confirmed several times during observations in the field. A study carried out by MSF in Y:men in 2013 showed that the decision to record incidents in SINDY (particularly less serious ones) varied according to whether the person in charge of inputting this data was at the start or end of their mission and whether or not they wished to notify the office in the capital and head office. See Chapter 6, box: “The Case of ‘Dangerous Patients’ in Yemen’s Governorate of Amran”, p. 103.—all the more because it concerns a small number of very disparate incidents, which results in data devoid of any real statistical significance. And lastly, shrinking the description of each event to make it fit into a generic nomenclature (“theft”, “threat”, “kidnapping”, etc.), the quantitative description of incidents impoverishes their understanding and masks each one’s particular significance. By way of example, SINDY aggregates into the same category “threats” made by ISIS militants against MSF volunteers suspected of spying, “threats” made to a field coordinator by a representative of striking staff in CAR and “threats” issued against a doctor by the parents of a patient admitted to the Khamer hospital in Yemen. All threats but, needless to say, all completely different, as much in the dangers they pose as in how they should be responded to. Similarly, a quantitative approach to “severe security incidents” allows some MSF security focal points to congratulate themselves on a numerical stability that conceals the unprecedented severity of kidnappings that occurred in 2014.
Just as MSF is investing in building databases on security incidents—in line with the rest of the humanitarian aid sector—the usefulness of such data is being challenged by sectors as sensitive as nuclear energy and air traffic safety.See Eric Marsden (ed.), “Quelques bonnes questions à se poser sur son dispositif REX”, Les Cahiers de la sécurité industrielle 2014-01, Fondation pour une Culture de Sécurité Industrielle, pp. 23, https://www.foncsi.org/fr/publications/collections/cahiers-securite-industrielle/bonnes-questions-REX/CSI-REX-bonnes-questions.pdf/view, last accessed 29 December 2015.
For instance, Eurocontrol (the European Organisation for the Safety of Air Navigation) no longer evaluates the safety of air traffic control operations on the basis of incident data, preferring instead qualitative operational and performance indicators.Fassert, op. cit., pp. 249-272.It notably encourages dialogue between different air traffic control authorities to share information and experience about events occurring on a daily basis, with particular emphasis on particular critical incidents, the importance and severity of which go unnoticed in databases.
In reality, the main advantage of SINDY is to provide a technical solution for systematic and central archiving of incident and accident reports involving national and international personnel. It has yet to serve a useful purpose, i.e. to calculate simple and clear indicators, such as the number of fatal accidents or the number of accidents resulting in sick leave (inexplicably absent from the summary tables currently proposed by SINDY)Also could be included: “number of days detained”, “number of vehicles stolen/ returned”, “value of property destroyed or stolen”.
and to examine and discuss the most serious events based on rigorous qualitative analyses. In this respect, what is lacking at MSF and other humanitarian organisations is not so much a statistics bureau but rather an entity similar to France’s civil aviation Bureau d’enquete et d’analyse (BEA, Bureau of Investigation and Analysis), whose mission is:
“To conduct neutral investigation, whose sole purpose is to collect and analyse relevant information, to determine the circumstances and the likely or possible causes of the accident or incident, and, if relevant, to produce safety recommendations to prevent future accident and incident from happening.” http://www.bea.aero/fr/bea/information/information.php. See http://www.bea. aero/fr/bea/information/information.php, last accessed 29 December 2015.
***
Humanitarian Security Manuals: Neutralising the human factor in humanitarian action
Monique J. Beerli and Fabrice Weissman
As described in previous chapters, security-oriented transformations implemented in the past twenty years have left their mark on humanitarian practice. Against this backdrop, the role of “humanitarian security” manuals in formalising security policies and procedures within the humanitarian sector has been significant.
First appearing in 1993 as a series of short pamphlets, in 1999 the ICRC published Staying Alive, which included a set of guidelines on how to behave and what to be aware of in a conflict zone, detailed descriptions of weapons used in conflict, and guidance about how to minimise physical harm when under attack.David Lloyd Roberts, StayingAlive: Safety and Security Guidelines for Humanitarian Volunteers in Conflict Areas, Geneva: ICRC, 1999.
In 1995, Save the Children UK released a guide entitled Safety First,Mark Cutts and Alan Dingle, Safety First: Protecting NGO Employees Who Work in Areas of Conflict, 2nd ed., London: Save the Children, 1998.
the first of its kind by an international NGO to be entirely devoted to security. Safety First addressed topics such as the use of humanitarian principles in protection strategies while providing an introduction to security management practices and an overview of practical protection measures.At the beginning of the 1990s, as part of a general guideline on administrative and logistical issues, MSF also established its first set of security “Golden Rules”, along with practical recommendations on how to build a bomb shelter, move around and manage communications in insecure environments. See Chapter 2, p. 21.
Subsequent to the Great Lakes crisis, the first security training modules were developed in 1996 as part of a collaborative effort between the United States Agency for International Development/Office of U.S. Foreign Disaster Assistance (USAID/OFDA) and InterAction. This initiative laid the foundation for what in 2000 became Good Practice Review Number Eight (GPR 8), edited by Koenraad Van Brabant on behalf of the Humanitarian Policy Network at the Overseas Development Institute (ODI, London). Entitled Operational Security Management in Violent Environments,Koenraad Van Brabant, Good Practice Review 8: Operational Security Management in Violent Environments: A Field Manual for Aid Agencies, London: Overseas Development Institute, 2000.the GPR 8 was designed “as a practical reference tool [for] field-level aid agency managers [offering] a systematic step-by-step approach to security management starting from context analysis and threat and risk assessment, to security strategy choice and security planning.”
Coordinated by consultants from Humanitarian Outcomes, in 2010 a larger group of experts revised and republished the GPR 8.Adele Harmer et al. (eds), Good Practice Review 8: Operational Security Management in Violent Environments, revised ed., London: Overseas Development Institute, 2010.
The revision process called on some thirty contributors and reviewers, with representatives from twenty NGOs (including MSF), three United Nations agencies (UNICEF, UNWFP, UNDSS), three institutional donors (USAID, ECHO, DfID) and seven private companies with connections to security (insurance, corporate security, telecommunications, etc.). Considered a “seminal document in humanitarian operational security management”Harmer et al. (eds), op. cit., p. 1.
and often referred to as the “bible” of humanitarian security, the GPR 8 has, since its release in 2000, influenced the burgeoning array of security manuals published by relief organisations themselves, donors and professional networks of security experts.
Drawing primarily on the 2000 and 2010 editions of the GPR 8, this chapter provides a general description of the content and the policy recommendations enshrined in security manuals in order to address the following issues. According to these guidelines, why does security need to be professionalised and institutionalised? What is security and how are humanitarians to be protected? What are the preferred solutions to the challenges they confront in the field? The chapter then highlights some of the underlying assumptions and values conveyed in such technical manuals.
Justifying the Call for Security Professionals
Most specialised manuals put forward three arguments to justify the introduction of security expertise into the humanitarian sector. First, replaying highly mediatised events and citing selective statistical data,See Chapter 4, p. 55. many manuals argue that “the number of incidents affecting aid agencies has risen significantly” and the “overall respect for aid agencies and therefore for the ‘immunity’ of its staff has significantly decreased in recent years.”Koenraad Van Brabant, “Mainstreaming the Organisational Management ofSafety and Security. A Review of Aid Agency Practices and a Guide for Management”, London: Overseas Development Institute, March 2001, p. 16. As reiterated in the most recent Save the Children (SCF) security guidelines, “[t]he tragic deaths of our aid worker colleagues in recent years highlight the unprecedented levels of hostility and violence to which we are increasingly exposed in the course of our work.”Shaun Bickley, Safety First: A Safety and Security Handbook for Aid Workers, 2nd ed., London: Save the Children, 2010, p. vii.Alongside discourses on the new era of global humanitarian insecurity and the unparalleled complexity of contemporary crises, present-day manuals also call on legal and ethical arguments. “Ultimately, security management in highrisk areas is both a moral and a legal obligation”, argues the revised edition of the GPR 8.Harmer et al. (eds), op. cit., p. 1.
In the 1990s, legal frameworks were more commonly evoked to stress the responsibility of host countries, their obligations under international humanitarian law and those of other legal entities granting protection and immunity to international civil servants and humanitarian workers.Office of the United Nations Security Coordinator, Security in the Field: Information for Staff Members ofthe United Nations System, New York: United Nations, 1998, p. 1.
However, the law is currently used as a means to pressure organisations into instituting and applying security experts’ recommendations:
"The legal requirement of duty of care of the employer is becoming increasingly important. Many countries have labour laws that impose obligations on employers to ensure safety in the workplace. Although such obligations have rarely been considered in the context of international aid work, aid organisations are open to growing legal challenges if they fail to properly inform staff about the risks associated with a particular assignment, or fail to take all necessary measures to reduce those risks."Harmer et al. (eds), op. cit., p. 7.
Lastly, most security manuals argue that security management cannot be allocated to “managers who lack the requisite skill or competence.”Van Brabant, Good Practice Review 8: Operational Security Management in Violent Environments: A Field Manual for Aid Agencies, op. cit., p. 9.
“Security management, like gender and the environment, can be regarded as a specialist area. It definitely needs expertise.”14. Ibid., p. 6.
Aid organisations need to “incorporate the externally developed expertise into in-house knowledge.”Van Brabant, “Mainstreaming the Organisational Management of Safety and Security: A Review of Aid Agency Practices and a Guide for Management”, op. cit., p. 50.
It would be dangerous to rely on managers whose security competence is grounded solely on longstanding operational experience, as “field experience from a world in which there were fewer threats, greater respect for aid organisations and a habit of risk taking may actually be a liability rather than an asset when it comes to security management.”Ibid., p. 49.The author of the first edition of the GPR 8 complained in 2001 that, despite these compelling arguments, some humanitarian organisations were still reluctant to professionalise security management in accordance with the recommendations provided in good practice manuals. Among other reasons, he mainly attributed resistance and hesitation to the conservatism, blindness, incompetence, cynicism, arrogance and mental instability of senior and midlevel humanitarian managers. Their attitudes were characterised as follows:
"- The dinosaur reflex: “We can continue doing what we did in the past”.
- The ostrich reflex: head in the sand and hope the problem will go away.
- The armchair mentality: non-appreciation of the reality because too far removed from it.
- The accountant reflex: “How are we going to fund this?” “Not if it costs a lot”.
- The ignorance or false-knowledge syndrome. (...)
- A discriminatory attitude: “International staff are capital assets, national staff are expendables.”
- The career-first mentality: keep quiet about training needs, management weaknesses and even incidents if they might negatively affect chances of promotion.
- The adrenaline-addict syndrome: risk-taking gives a thrill.
- The A-type personality: action-oriented, highly driven, hard to restrain.
- Solidarity under threat: “Stay with endangered populations even if you can’t do much to protect them.”Ibid., p. 17.Nonetheless, ten years later, the authors of the revised edition of the GPR 8 asserted that the humanitarian sector was slowly succumbing to the claims and policy initiatives of security experts and manuals, “giving rise to a growing professionalism and sophistication in humanitarian security practices and interagency coordination.”Harmer et al. (eds), op. cit., p. 1.
Overcoming Danger: Calculability, Planning and Self-Discipline
Few manuals offer a precise definition of what they mean by “security” and “good security management”. Seemingly the first attempt to define these terms, the GPR 8 identifies “security” as “freedom from risk or harm resulting from violence or other intentional acts.”Harmer et al (eds), op. cit., p. xviii
The scope of potentially harmful situations that have to be taken into consideration differs between the two editions of the GPR 8. While the first edition limits the reach of security management to the “protection of aid personnel and aid agency assets from violence”,Van Brabant, Good Practice Review 8: Operational Security Management in Violent Environments: A Field Manual for Aid Agencies, op. cit., pp. xii-xiii. the revised edition extends protection to the aid agencies’ “programmes and reputation.”Harmer et al. (eds), op. cit., p. 7.
As in the corporate sector, security management in the aid world appears now to encompass the protection of an agency’s personnel, property and activities as well as the defence of its image.
The GPR 8 and other such manuals remain ambiguous regarding the desired end state that “good operational security management” is meant to achieve. More or less explicitly recognising that “freedom from risk” is an unattainable objective in war zones, there is a tendency to identify good security management with an absence of “unjustified risks”, as illustrated in the introduction to the GPR 8 (2010):
"good operational security management means asking whether the risk is justified in light of the potential benefit of the project or programme, and whether everything possible has been done to reduce the risk and the potential impact of an incident."Ibid., p. 3.
The absence of unjustified risk is equated with the implementation of the recommendations set out in the manuals—except, explains (in a kind of disclaimer) the introduction to the GPR 8, when the “circumstances” and one’s “situational judgment” prescribe “do[ing] something very different from or even contrary to” the advised course of action.Ibid., p. 7.
From Empowering Staff" to Managing (In)security
Emerging in the mid-1990s, the first generation of security manuals were primarily aimed at producing a single-source document outlining “need-to-know” information for individuals as they got “used to operating in war-zones.”Cutts and Dingle, op. cit., p. 11.
For example, the ICRC’s security pamphlets, its Staying Alive guidelines and Save the Children UK’s Safety First primarily embraced an ‘awareness approach’, distinguished by the central claim that “[s]ecurity starts with the individual.” Safety First was intended as a “reference source to remind [NGO employees] of what to look out for and the questions [they] should be asking [themselves].”Ibid. This style of manual mainly included “tips” to help field personnel confront the hazards of war zones (how to use radio and satellite communications, how to protect vehicles, cope with the threats posed by landmines, respond in the event of an attack, etc.). In explaining how to use the manual, the author of Staying Alive even insists on the need to “combine the contents of this book with your own common sense and judgment”Lloyd Roberts, op. cit., p. 16.
This first generation of manuals included a loose notion of what “successful” risk management required from organisations.Charles Rogers and Brian Sytsma, A Shield About Me: Safety Awareness for World Vision Staff, Monrovia, CA: World Vision, 1998, Cutts and Dingle, op. cit.
Suggestions included hiring experienced staff, providing support services for employees, ensuring equipment was in good working order and giving clear guidelines for staff actions, but did not expand upon these points. A more in-depth and exhaustive approach to security management emerged with the publication of the GPR 8 in 2000. Arguing that “organisational failure cannot be a disproportionately contributing factor to injury or death”, this good practice guide explicitly claims that “what is missing is a ‘management approach’ to security—something that this GPR attempts to offer.”Van Brabant, Good Practice Review 8: Operational Security Management in Violent Environments: A Field Manual for Aid Agencies, op. cit., p. 9.
Assessing the Risks
The GPR 8 security management framework adopts a general structure mirroring that of the project management cycle: “Assess, plan, implement (and adjust if needed), review and reassess.”Harmer et al. (eds), op. cit., p. 8.
In order to assess the risks, the GPR 8 sets out a series of steps, starting with a programme analysis (“the identification of ‘who you are’ and ‘what you do’”)Ibid., p. 35.
and a situational analysis (a general understanding of the history and current dynamics of the conflict, society and culture, crime, infrastructure and climate).Van Brabant, Good Practice Review 8: Operational Security Management in Violent Environments: A Field Manual for Aid Agencies, op. cit., pp. 22-25.
Organisations are then expected to proceed with a detailed contextual analysis (i.e. an analysis of the actors, political and military developments, political economy of armed groups and mapping of violence)Ibid., pp. 26-35.
and to follow up with a threat assessment.
The latter is defined as “the attempt to examine more systematically the nature, origin, frequency, and geographical concentration of threats.”Ibid., p. xiv; Harmer et al. (eds), op. cit., p. xix.
Threats to be considered include crime (car-jacking, road banditry, street robberies/ muggings, armed raids/robberies, kidnapping), terror attacks (IEDs, car/ truck bombs, suicide bombers in vehicles, bombings and gun attacks in public places, grenade attacks on compounds, hostage-taking) and combat/military activity (shelling, infantry crossfire, landmines).Harmer et al. (eds), op. cit., pp. 39-40.
In order to better understand the context and its threats, and to “predict the kind of incidents that may be likely in the future,”Ibid., p. 101.
the revised edition of the GPR 8 recommends compiling incident databases:
"A reliable overview of reportable incidents around the world, worked through a database, allows for greater security analysis at the country, regional and global levels. (...) [Such a system] can reveal geographical concentrations of incidents, provide insight into the types of incidents taking place and show whether the overall number of incidents is increasing or decreasing."Ibid., p. 101.
Based on these analyses, organisations may be expected to produce a risk assessment culminating in a risk matrix plotting and ranking “threats and vulnerabilities” according to their “probability and impact.”Ibid., p. 29.
This process must be conducted “in a structured and disciplined manner” in order to supress the inherent subjectivity of human nature that “can create a distorted picture reflecting our unconscious bias.”Ibid., p. 27.
Elaborating the Strategy
After the risk assessment comes the security strategy. Conceptualised for the first time in the GPR 8, three ideal types of strategy are proposed, each with their own “overarching philosophy, application of approaches and use of resources that frame organisational security management”: acceptance, protection, deterrence.Ibid., p. xviii.
The acceptance strategy is understood as a means to remove or negate threats by “building relationships with local communities and relevant stakeholders in the operational area, and obtaining their acceptance and consent for the organisation’s presence and its work.”Ibid., p. xv.
Managing perception (and more particularly challenging the perception of aid agencies as “instruments of the Western foreign policies and Western values”)Ibid., p. 60.
is described as a key component of a successful acceptance strategy. As such, it implies “maintaining] internal and external consistency in communication”,Ibid., pp. 60-61.
at the local and global level. This is especially important in a globalised world where an increasing number of people have access via the Internet and social media to information about an agency and public statements made on its behalf. The revised edition of the GPR 8 insists that:
"the website, a spokesperson at headquarters and a staff member talking to local media on the ground all say the same thing. All staff, from senior managers to guards and drivers, need to be able to understand and communicate the goals and principles of the organisation. (...) One way to ensure that staff are able to communicate these messages is to develop a simple Question and Answer sheet. (...) If possible, control the final version that goes into the public domain: for example, the content of a written press release is easier to keep under control than a press conference that allows questioning, or a live interview. Beware also of “leaked” statements"Ibid., pp. 61-63.
In addition, agencies should avoid “public criticism” since “critical public statements are seldom received with gratitude.”Ibid., p. 62.
"The pursuit and preservation of acceptance may require that agencies stay silent about humanitarian or human rights abuses. Speaking out may create security risks on the ground, or may lead to the agency’s expulsion."Ibid., p. 68.
More generally, the GPR 8 describes encounters with journalists as a potential source of danger:
"A poorly worded, inaccurate or inflammatory statement can put staffin direct danger and may even result in expulsion from a country. (,..)In some situations, the role of international agencies may be so contentious that drawing further attention to it by working with the media would be counter-productive. In this case, develop a good defensive strategy, either refusing to comment, limiting remarks to basic factual information or clarifying misinformation by issuing short reactive statements."Ibid., pp. 159-160.
While considering acceptance as “the most appealing security strategy” for humanitarian organisations, the GPR 8 encourages agencies to combine it with “protection and deterrence approaches.”Van Brabant, Good Practice Review: Operational Security Management in Violent Environments: A Field Manual for Aid Agencies, op. cit., p. 56.
A protection strategy “tries to reduce vulnerability in two ways, either by hardening the target or by increasing or reducing its visibility.”Harmer et al. (eds), op. cit., p. 71.
As for the deterrence approach, it “attempts to deter a threat by posing a counter-threat: essentially discouraging would-be attackers by instilling fear of the consequence they may face.”Ibid., p. 73.
In its most extreme form, it implies the use of armed force. Other forms of deterrence are equally considered, such as the use of legal and diplomatic leverage, the suspension of operations or withdrawal as well as support and protection from “local strongmen.”Ibid., p. 74.Interestingly, the GPR 8 does not consider the use of public pressure or speaking out as possible deterrents, therefore reducing communication and journalists to potential sources of danger rather than protection.
Standardising Procedures and Behaviours
Lastly, a security strategy is implemented, primarily through the application and enforcement of standard operation procedures (SOPs): “Formally established procedures for carrying out particular operations or dealing with particular situations, specifically regarding how to prevent an incident happening, survive an incident or follow up on an incident as part of the agency’s crisis management planning.”Ibid., p. xix.SOPs are generic procedures, ranging from what to do in the routine day-to-day to how to manage an evacuation, report a critical incident and deal with specific threats.
The GPR 8 insists that any security strategy will be undermined if the staff does not have the “behavioural self-discipline”Ibid., p. 115.
to comply with the SOPs and other regulatory rules, such as codes of conducts (including codes of sexual conduct). “Irresponsible staff (...) being dismissive about security procedures or overconfident that they can handle any security situation because they have done so for many years” are categorised as a threat as much to themselves as to their colleagues. In order to tame or subdue such behaviours, “security procedures may have to be mandatory, and breaches made a disciplinary offence.”Ibid., p. 124.
In the same vein, staff displaying symptoms of “negative stress”, such as “substance abuse, notably caffeine, alcohol, cigarettes and perhaps drugs, a series of short and casual romantic relationships or unprotected sex”,Ibid., p. 131.
may be unable or unwilling to comply with SOPs and codes of conduct. While it is up to individual staff members to manage their own stress, it is the manager’s responsibility to remove staff whose “negative stress” represents a threat both to themselves and to others.
The Implicit Ideology of Security Manuals
Although presented as neutral tools, technical manuals such as the GPR 8 and other security reference books peddle a succession of representations and beliefs. As suggested by Giovalucchi and Olivier de Sardan when discussing “logical frameworks” used by development agencies for the conception and planning of projects, “any public policy instrument carries more or less explicit meanings in terms of political vision and cognitive models. In other words, it conveys a certain ideological and epistemological configuration engrained in its technical structure.”François Giovalucchi and Jean-Pierre Olivier de Sardan, “Planification, gestion et politique dans l’aude au développement: le cadre logique, outil et miroir des dével¬oppeurs,” Revue Tiers Monde, 2, No. 198 (2009).
Valorising the Institution
First, the new generation of security manuals conveys an extended notion of security that identifies the institution itself as a value worth protecting. Security measures are therefore not limited to the protection of a humanitarian organisation’s staff, assets and operations but also the defence of its reputation and institutional interests.
The Predictability and Calculability of Danger
Moreover, juxtaposed to a “personal sense of security”, described as a “subjective and therefore potentially misleading form of threat and risk assessment relying on one’s personal impressions of a situation”,Van Brabant, Good Practice Review 8: Operational Security Management in Violent Environments: A Field Manual for Aid Agencies, op. cit., p. xii.
security management frameworks are depicted as tools capable of producing “objective” and “scientific” analyses, policies and procedures, thereby overcoming the propensity for human error. This is particularly true with regard to risk analyses. Conceptualised as a mathematical function, i.e. risk = likelihood (threat, vulnerability) x impact,Harmer et al. (eds), op. cit., p. xviii. it is presumed that danger can be calculated through a methodical analysis coupled with the cross-referencing of variables. Whether articulated as numerical or categorical typologies, illustrating risk in such terms gives an impression of the precision, exactness and certainty of its measure, in sharp contrast with the uncertainty so rife in conflict situations.
People as Sources of Danger
Associated with this positivist approach, manuals such as the GPR 8 contribute to the discrediting of individual judgment and initiative. Whereas the awareness approach of the mid-1990s valued the individual and their capacity to adapt to new environments, the “management approach” tries to eliminate or minimise the role of the individual through the modelisation of security and risk. In doing so, field personnel become constructed both as threats to themselves and to others and, as a consequence, are subject to a form of disciplinary power or control limiting the scope of their actions and their forms of expression.
In addition, security management frameworks provide a particular vision of the countries where humanitarians operate. While NGO annual reports, publicity campaigns and websites display images of vulnerable, suffering populations in need, risk analyses and their resultant risk maps and lists of high-risk countries relay a frightening portrayal of these countries and their inhabitants. Host countries and even beneficiaries are presented as sources of risk and insecurity for humanitarian operations and their personnel. In contrast, aid workers are seen merely as “good people doing good work.”“Introduction”, Robert Macpherson and Bennett Pafford, Care International Safety Coupled with this negative portrayal, field personnel are told to “[b]e aware and suspicious. Look for the unusual. [...] Presume that you may be a victim.”UNSECOORD and UNHCR, Security Awareness: An Aide-Mémoire, Geneva: UNHCR, 1995.
As such, manuals encourage humanitarians and NGO employees to scrutinise their operating environments through a lens of suspicion and fear.
Insecurity as a Technical Problem and the Expert as a Remedy
This view of populations in danger as dangerous populations is combined with an apolitical conception of security issues. The acceptance paradigm assumes that a humanitarian agency’s security relies primarily on perception rather than on political transactions—that it suffices to be perceived as “good people doing good work” in the name of universal values. This denial of politics is well illustrated by recommendations concerning public communication, which is either viewed as a marketing tool to promote the moral and social value of humanitarian actors or, at the other end of the spectrum, as a potential source of danger.
Lastly, shunning politics goes hand in hand with the promotion of security management as an area of expertise. Manuals such as the GPR 8 participate in the transformation of security into a specialised knowledge and the monopolisation of that knowledge by a specific corporation of “professionals”. As such, the GPR 8 functions as an “anti-politics machine”, transforming inherently political decisions related to security into “technical solutions to technical problems.”James Ferguson, The Anti-Politics Machine: “Development”, Depoliticization, and Bureaucratic Power in Lesotho, Cambridge: Cambridge University Press, 1990.
In summary, this corpus of humanitarian security manuals forms a coherent and reassuring narrative that can be resumed as follows: “The world is increasingly dangerous for humanitarian organizations, which are both legally and morally responsible for the security of their personnel. But these dangers can be overcome (and aid organisations can be protected from legal and reputational risks) through the objective measurement of risks, the rational planning of security strategy and the standardisation of aid workers’ behaviours and public expression.” The power of this narrative allows aid organisations to conceal the security dilemmas arising from operating in dangerous situations, while justifying the need for authoritarian control over their personnel in the name of security.
***
BOX: Who Benefits from “Duty of Care” ?
Jonathan Edwards and Michaël Neuman
“I am somewhat worried that by elevating our duty of care obligations to a level that may meet liability standards in home societies we risk fundamentally sabotaging our operational mission.”
MSF Operations Manager, 2015
Rooted in the common law legal system, the principle of duty of care is broadly defined as an employer’s duty “to take reasonable steps to provide a safe system of work to avoid the risk of reasonably foreseeable injury, whether physical or psychiatric.”External legal advice to MSF-Australia, 2014.
This approach dates back to nineteenth-century Britain when reaction to appalling rates of morbidity and mortality in factories and mines led to the introduction of a series of health and safety laws and regulations that included access to compensation for injured workers. This legal and regulatory framework advanced throughout the twentieth century, consolidating during the 1970s into the “workplace health and safety” regimes that wield such influence on societal understanding of risk and liability issues, particularly in English-speaking countries.Ian Eddington, An historical explanation of the development of occupational health and safety and the important position it now occupies in society, Brisbane : Queensland Safety Forum, January 2006.Similar provisions exist in continental Europe where they are embedded in the labour laws of various countries.And internationally, as seen in the International Labour Organisation’s Occupa¬tional Health and Safety Conventions of 1981 and 2006.
French civil labour law, for instance, stipulates that employers (French or otherwise) have the general obligation to ensure a safe working environment for their employees: “The employer shall take all the necessary measures to ensure the safety, and to protect the physical and mental health of workers.”French Labour Code, L-4121-1.
Employers thus have the obligation to assess and manage any foreseeable risk. French case law has gone on to develop a broad interpretation of this obligation, regardless of the level of risk employees may be subject to.Cour de cassation, judgment n°2575, 7 December 2011, Société Sanofi Pasteur/ Peyret”.
As for other high-risk occupations, laying out the practical implications of duty of care from the practitioner’s perspective is particularly challenging, as, by definition, the act of providing relief in situations of conflict involves an exposure to risk. In 1997 and 2003, the NGO consortium People in AidA network of international humanitarian aid and development agencies.
set out a “Code of Best Practice” to define the employer’s obligations under duty of care : briefing staff on the situation in the place they are to be assigned to, keeping records of work-related injuries, accidents and fatalities and performing regular reviews of security procedures. These norms in duty of care have now been widely adopted by aid agencies as standardDuty of care was one of the ten Humanitarian Accountability Project Standard Principles first drafted in 2007. The ICRC began to formally adopt duty of care language in 2009 after a series of critical incidents.
and feature regularly in discussions on best practices in human resources management for humanitarian organisations.For example, Humanitarian HR Conference Europe 2012, “What Duties? Who Cares ?”, Amsterdam, and InterAction Duty of Care symposium 2014, Washington D.C., which included a presentation by MSF-Holland’s HR manager.
Yet the duty of care frame still raises key questions around the potential practical and legal implications, which need to be evaluated on a case-by-case basis as they depend as much on the contexts of intervention as on national legal frameworks.
While originally introduced into the aid sector as a good practice standard in human resource management, “duty of care” is increasingly considered from the legal and liability perspective. “Can you get sued?”, a review conducted by Geneva-based think tank Security Management Initiative in 2011, examined international aid organisations (IAOs) with legal obligations under both common law jurisdictions and European strict liability and concluded that, despite a growing awareness of legal responsibilities towards staff, “serious gaps exist between legal requirements and current practice as to employer obligations.”Edward Kemp and Maarten Merkelbach, “Can you get sued? Legal liability of international humanitarian aid organisations toward their staff”, Policy Paper 74, Geneva: Security Management Institute, 2011, p. 17. More precisely, they point to a majority of the IAOs interviewed as lacking “a proper occupational health and safety protocol”, 30 per cent any “institutionalised security management and reporting” and 66 per cent without a budget allocated expressly to security. Organisations that have not decided to consider security as a fully-fledged professional sector are thus deemed to be legally at fault. Drawing from recent legal cases in the commercial sector,See the “Karachi litigation case”.
the authors also warn of the possible damages that could be awarded if judgments are made against organisations found to be in some way negligent. In the same vein, the authors, one of whom is specialised in employment law and personal injury law, urge aid organisations to seek legal advice, conduct routine risk analyses, and design and implement risk mitigation procedures. Though scarcely able to produce more than one case of judicial liability in the past thirty-five years,See Samaritan’s Purse vs Flavia Wagner, http ://www.reuters.com/article/2011/ 05/19/us-newyork-kidnap-idUSTRE74I70A20110519, last accessed 30 Decem¬ber 2015. However, as Carolyn Klamp has pointed out, the low number ofreported cases could be due to the prevalence of confidential legal settlements. Carolyn Klamp and Associates, “Duty of Care”, RedR Safety and Security Review Issue 7,
unsurprisingly, the authors insist on the need to implement systems recommended by experts to analyse and mitigate risk.See Chapter 5, p. 71.
This approach, as the title “Can you get sued?” suggests, sets out as much to protect an organisation from liability risks as to protect an individual employee from danger. Opinions across the MSF movement still differ regarding the significance and implications of the ever-increasing focus on duty of care prevalent in Western society, and more particularly in the aid sector. Operational managers are more likely to highlight the risk of compromising MSF’s operational scope through a narrow and bureaucratic understanding of the requirements of duty of care; board members from particularly litigious home countries are more sensitive to personal exposure to liability;For example, boards have voiced their concern regarding their liability in the event of international staff becoming fatally infected with Ebola and, less urgently, in relation to the exposure to asbestos of international staff working in the field. Jonathan Edwards, “Duty of Care in MSF”, Internal Report, Medical Care Under Fire, Paris: MSF, 2015.
and human resources managers are principally concerned with the operational sustainability gains to be found in properly implemented HR policies that care for their employees (and not simply their security). The debates are many, reflecting the far-reaching and contradictory ambitions of the concept.
But there are signs within MSF of an increasing focus on the legal dimension of duty of care. For example, during the response to the Ebola emergency in 2014, several MSF sections introduced a page-and-a-half-long assumption of risk and acknowledgement of liability form to be signed by international staff prior to leaving for the field. It includes the following clause:
I understand, acknowledge and accept that participation in an Ebola field mission, by its very nature, involves certain physical and health risks that cannot be eliminated regardless of the care taken to protect Ebola field mission staff. Those risks include the risk that I may contract Ebola. [...] I knowingly assume all such physical and health risks. [.] I understand that MSF is taking every precaution to protect me while I am participating in a Ebola field mission but that I am ultimately responsible for my health and my safety in the field.
The form ends with an “informed consent for medical treatment” clause, according to which staff “delegate to MSF [...] all power and authority” regarding potential medical treatment and management of care in the event that they contract or are suspected to have contracted Ebola during their assignment. This document is a manifest attempt to mitigate the threat of legal action. It makes clear that MSF has taken all necessary protection steps, thereby indicating that any contamination would be the responsibility of the contaminated person. Its introduction came within the somewhat exceptional context of an epidemic response suffused with a sense of danger for employees, their families and those around them that was deemed to be unprecedented. Nevertheless, it is hard to conclude that the sole objective of this expression of duty of care was to improve the safety of personnel; rather, it was a testimony to the progressively legal nature of the employee/employer relationship.
The pervasive interpretation of duty of care in terms of “institutional risk” is also found in the Volunteer Agreement that all volunteers employed by MSF’s French section have to sign prior to departing on mission. In addition to an already well-detailed contract, under the terms of which the volunteer commits to share in MSF’s Charter and “principles” and “acknowledges that he/she has been warned and is aware of the inherent risks linked to the mission allocated to him/her”, one annex stipulates that the volunteer commits “to observe and abide by the security rules and guidelines established by MSF and its representatives [...] and to comply with them at all times”. It is worth noting that this clause was recently reintroduced having been removed a few years ago when a number of staff members reacted negatively to it, finding it too prescriptive of their conduct. Partly a response by the management team to problems of misconduct, the reintroduction of this clause also reflects MSF’s willingness to regulate behaviour as a means of ensuring strict adherence to risk mitigation procedures such as those recommended in the legal advice discussed above.
Looking at the key indicators identified by People in Aid to assess aid agencies’ compliance with duty of care requirements in terms of security, it could be argued that MSF is a “responsible employer”. How far this translates to meeting duty of care obligations in legal terms is a matter of dispute as, again, the complexities of managing the legal environments for an organisation with employees from dozens of countries are staggering. And yet another critical issue is the status of national staff. Current inequities in the relationship between MSF as an employer and its workforce—as highlighted recently through the different levels of access to healthcare and support provided to international and national staff working with Ebola patients—must be challenged.
If organisations do not find suitable solutions themselves, then they may find them imposed by others, as in the case of Irish Aid’s “Guidelines for NGO Professional Safety & Security Risk Management”, which aim to help “NGO partners to fulfil their duty of care responsibilities towards their own staff”.“Guidelines for NGO Professional Safety & Security Risk Management”, Dublin: Irish Aid, 2013, p. 1.
These standards recommend appropriate recruitment, training, risk assessment, consent, mitigation measures and legal health and safety compliance for all staff. Deriving their influence from their link to accreditation and funding eligibility from Irish Aid, this “guideline” approach may well be widely replicated by other donors and governments. This has yet to happen, but if it were to be broadly adopted the implications for humanitarian organisations could be significant.
So the challenge facing MSF and other such organisations is to first define their own vision of this somewhat nebulous concept of duty of care and then to establish the extent to which it is being achieved. An organisation wide response to the question “what is your duty of care to your staff?” should not invoke an institutional risk mitigation approach, but leaving this issue to those managers closest to a mainstream and somewhat legalistic interpretation of duty of care, or to external regulators, risks doing exactly that.
Période
Newsletter
Subscribe to our newsletter to stay informed about our latest publications. Interested in a specific author or thematic? Subscribe to our email alerts.
